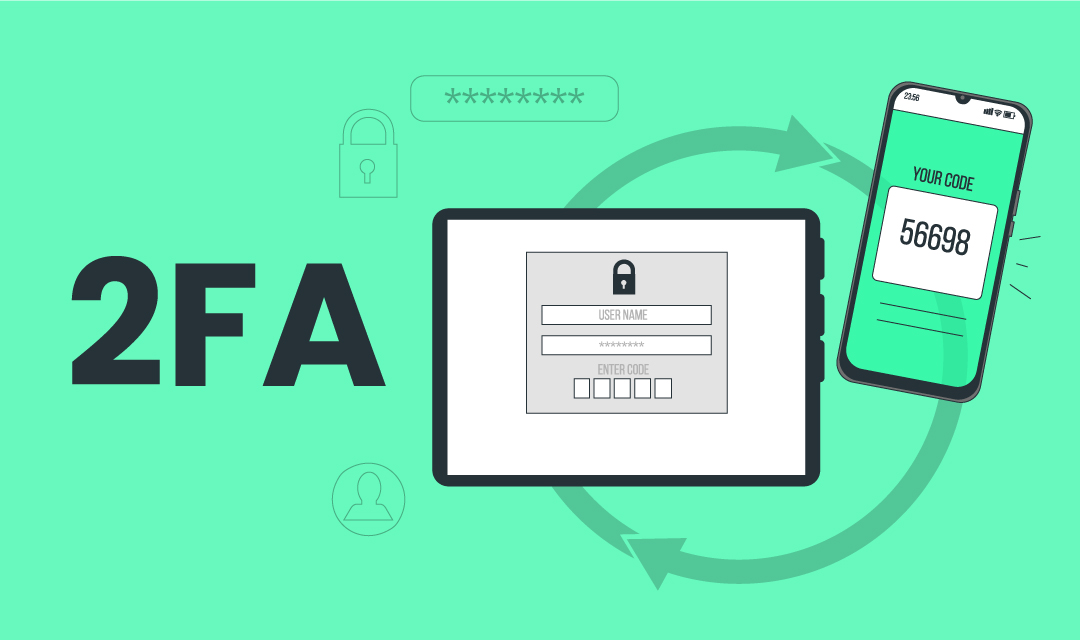
2FA (2-factor authentication) is a form of MFA where a user is required to supply 2 forms of authentication to allow access to the system. The traditional authentication system (or single-factor authentication) used the username/password pair to grant access to an account, but a growing number of hacking due to the use of weak passwords prompts the industry to offer an additional form of authentication to enhance the security of login access.
One earlier method that was used to supplement single-factor authentication is knowledge-based authentication, where users answer personal security questions, such as "What is your mother’s maiden name?" or "What is the name of your first pet?". However, this approach has shown weaknesses as personal information can often be found or guessed, particularly with the rise of social media.
Why use 2FA?
There have been a number of data breaches in an online community, and poor selection of weak passwords on user practices prompt service providers to offer a 2FA authentication system. Without using a password manager, users cannot remember strong passwords on every account without reusing the same password. Hackers obtain millions of breached username/password or email/password pairs and offer them for sale on the dark web making 1FA vulnerable and less secure.
In today's complex and busy world, we often use bank accounts and investment accounts online to transfer funds and make purchases of a large investment portfolio. Granting online access to your financial accounts to hackers may result in a devastating outcome. To protect your assets and online privacy, 2FA is needed and many individuals are signing up to secure their digital lives with 2FA.
Before 2FA was widely accepted, many financial organizations offered security questions to enhance the authentication system and it is still being used. The security questions were only asked if a user is signing in from a new computer or from IP location away from where the user usually logs in. Some of the common security questions include:
- What is your mother's maiden name?
- What is the name of your first pet?
- What was your first car?
- What elementary school did you attend?
- What is the name of the town where you were born?
Although this type of question helps tighten up the security initially, we soon learned that there are weaknesses to this approach. With the proliferation of social media, personal information is readily available online and it can be easily guessed.
What types of 2FA are available?
With username/password pair being used as a primary authentication system for several decades, the first factor is still the same. The second form factor is being added to enhance the security system, and this includes (1) something that you are, (2) something you have, or (3) somewhere you are. The example of second-factor authentication include:
- SMS Verification: This is similar to TOTP (Time-based One Time Password) where the user registers a mobile number when signing up, and the service provider sends a temporary passcode every time a user logs in.
- Email Verification: Similar to SMS, a temporary passcode is sent to the user's email address whenever a user tries to log in.
- Time-based Software Authenticator: You'll install an Android or iOS app on your phone, and authenticate yourself each time you're logging in. Authenticator apps generate time-based, one-time passcodes (TOTP) for two-factor authentication, enhancing security by requiring a second layer of verification during login. The service provider generates a QR code when the user registers, and the app stores this as a "seed" to generate an authentication code based on the current time. Since the code is generated by "seed" and time, the device that is generating the passcode must have a precise time, otherwise, the passcode will not work. The advantage of such a system is that you are no longer required to be online to generate the passcode. Examples of software authenticators include Google Authenticator, Microsoft Authenticator, and Authy to name a few.
- Biometric: Most smartphones offer facial recognition and fingerprints to verify a user's identity. Some notebook computers are equipped with fingerprints to bypass the username/password login.
- Physical Token or Authentication Key: Many companies involved in 2FA build physical U2F (Universal 2 Factor) devices that will generate an authentication token. The devices are either plugged into USB, and Lightning Cable or use NFC to generate the token. A few examples include Yubikey from Yuboco, Titan from Google, and FIDO U2F from Thetis.
- Google on-device prompts: This only works with Google accounts, but helps with second-factor authentication by acknowledging a prompt presented to your Android or iOS devices you own.
Conclusion
With the rise in cybercrimes in an online community, a stronger 2FA authentication system is needed to protect the user's security. With 2FA widely accepted and offered by many online service providers, users must enable 2FA and choose an available authentication mechanism offered by the provider. The primary authentication method is still the username/password pair, but a variety of second-factor authentication is offered.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.

Comments (0)
No comment